Bastion Server Set Up (Alt)
Setting up a bastion server for access to a non-AWS hosted database as a source
Context
Bastion hosts add an extra layer of security to the host architecture. It isolates your internal network from the Internet. Configured correctly, a bastion (sometimes called a Jump-box) is a secure way for controlled access to your VPC for an external service. Usually, the bastion host does act as proxy server. It allows and denies connection as created by your security policy. In this guide we will run through the steps needed to ensure that the kleene.ai application can securely and reliably connect to your database.
Visual Map of the architecture:
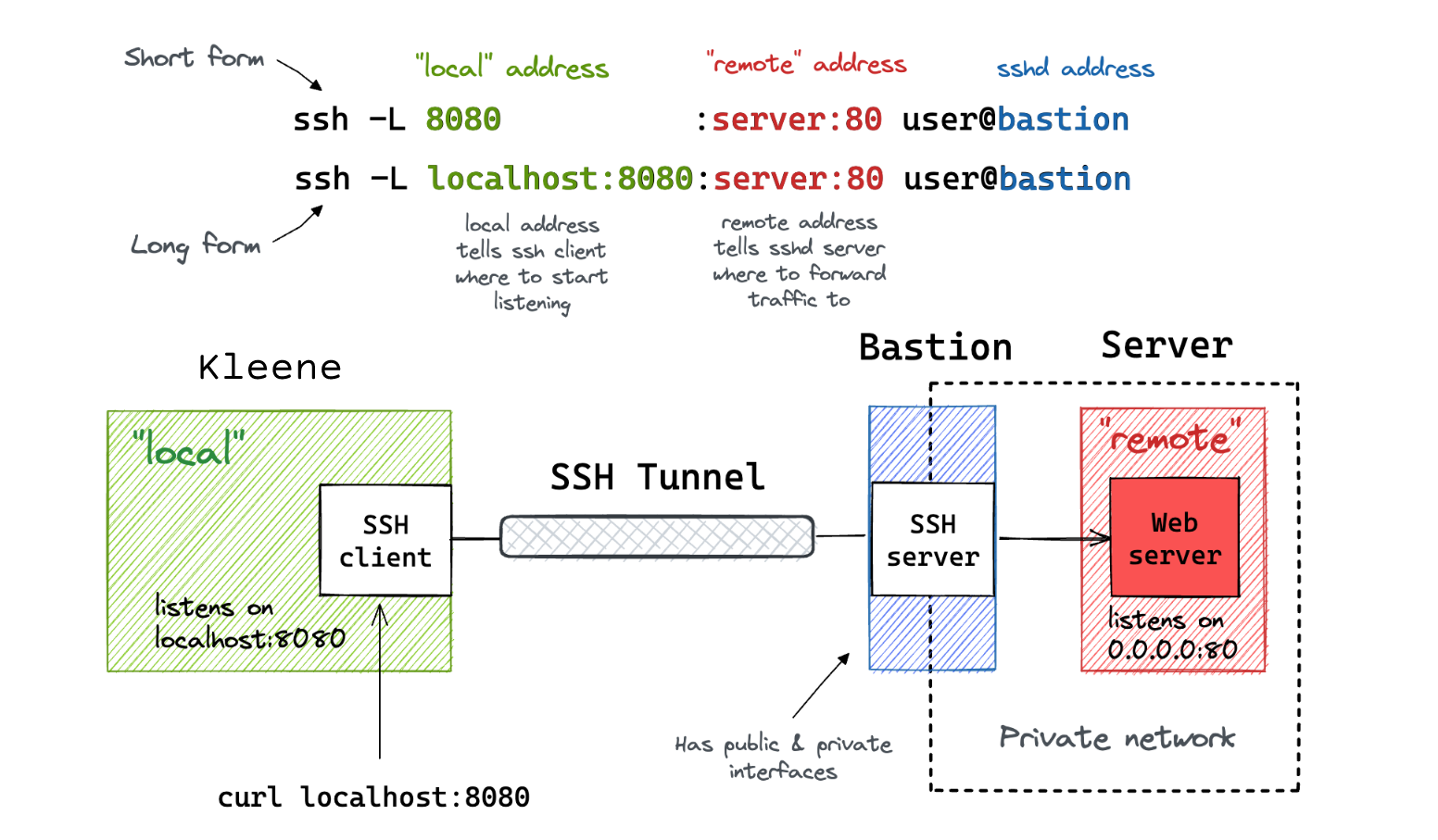
Visualisation by Ivan Velichko
How Do I Build Linux As a Bastion Host?
A Linux based bastion host can be build using the following steps:
- Grab your favourite Linux distribution e.g. Debian / CentOS CD.
- Install minimum operating system. Avoid installing desktop software or other apps such as MySQL, Apache and other software.
- Reboot the server.
- Patch server.
- Install grsecurity kernel patch and reboot the system.
- Install additional security software such as snort IDS and configure it.
- Install Advanced Intrusion Detection Environment (AIDE) Software.
- Make sure all security patches are installed.
- Disable all network services except ssh.
- Disable all other daemons.
- Network tuning vis sysctl.conf
- Configure firewall.
- Remove centralized authentication such as LDAP.
- Remove as many utilities and system configuration tools as is practical for your setup. No need to have gcc compilers and other unwanted tools. Use rpm/yum and dpkg command to list all packages.
- Logging of all security related events and turn on auditing.
- Write protect all log files and allow them in append only mode using chattr command (e.g. chattr +a /var/log/messages or chattr +i /etc/shadow).
- Encrypt all database passwords including file systems if possible.
- Create system recovery DVD or tape.
Above all are generic and recommended steps to configure bastion host.
External access to the bastion
Ensuring the bastion can be accessed by the kleene.ai application requires whitelisting the kleene.ai production IP in your relevant security group - please get in touch with your customer success manager so they can share with your the correct details for whitelisting.
Setting up authentication
The app uses key based authentication with SSH, so you will have to create a private .pem file which can be dropped into the connection setup screen in the kleene.ai app.
Confirming the connection
Add bastion and database credentials to kleene.ai application source screen and create a new database source.
To test whether this connection works, set up a new extract from this source and ensure that you can bring data back from the database server.
Once bastion access has been set up client side, the kleene interface will request the following details:
- Bastion Hostname
- Bastion User
- Bastion Pem Key
Updated about 1 month ago
